Device Control
Complete visibility and control over devices to safeguard your data and your business
REQUEST DEMO
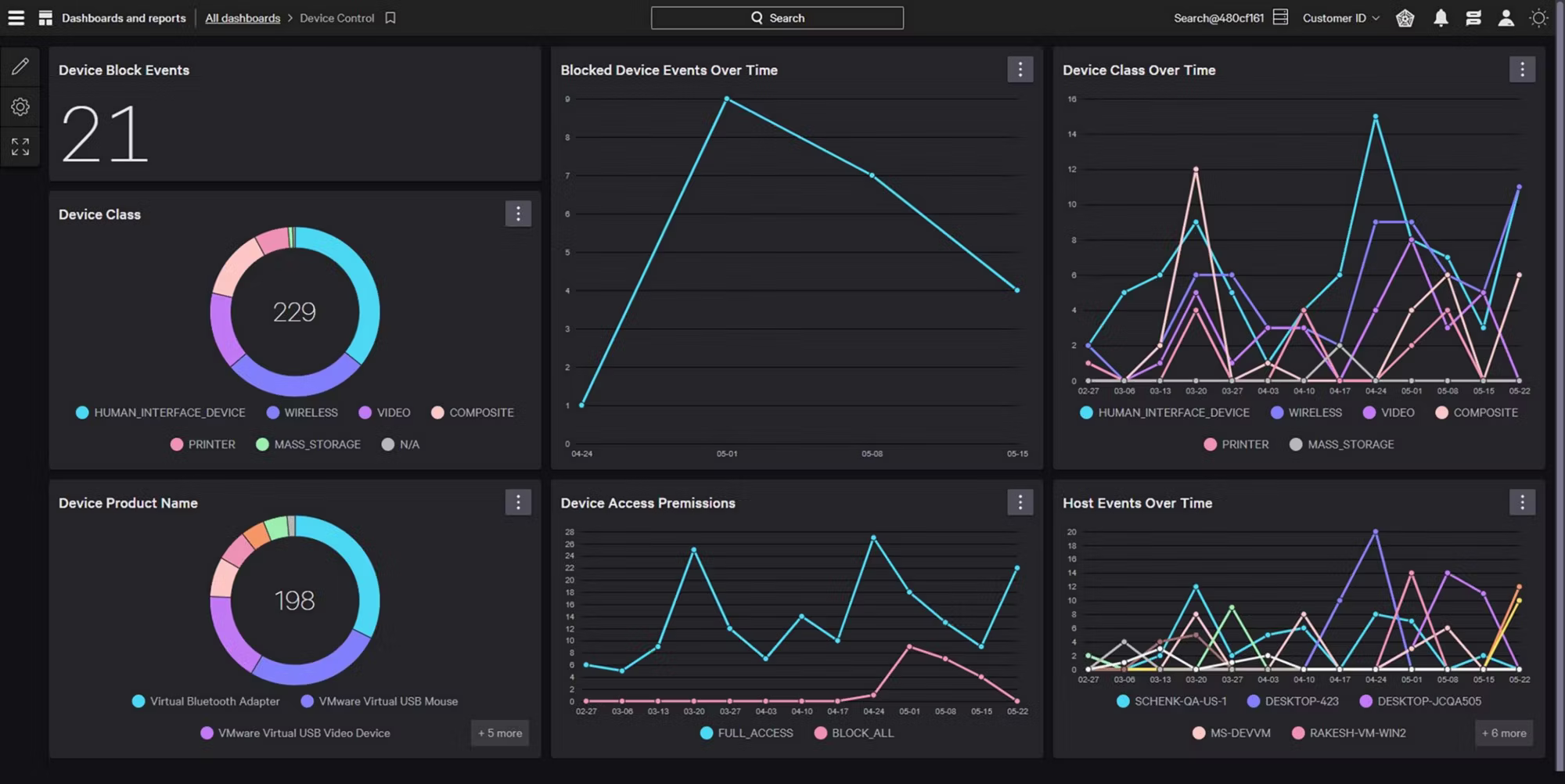
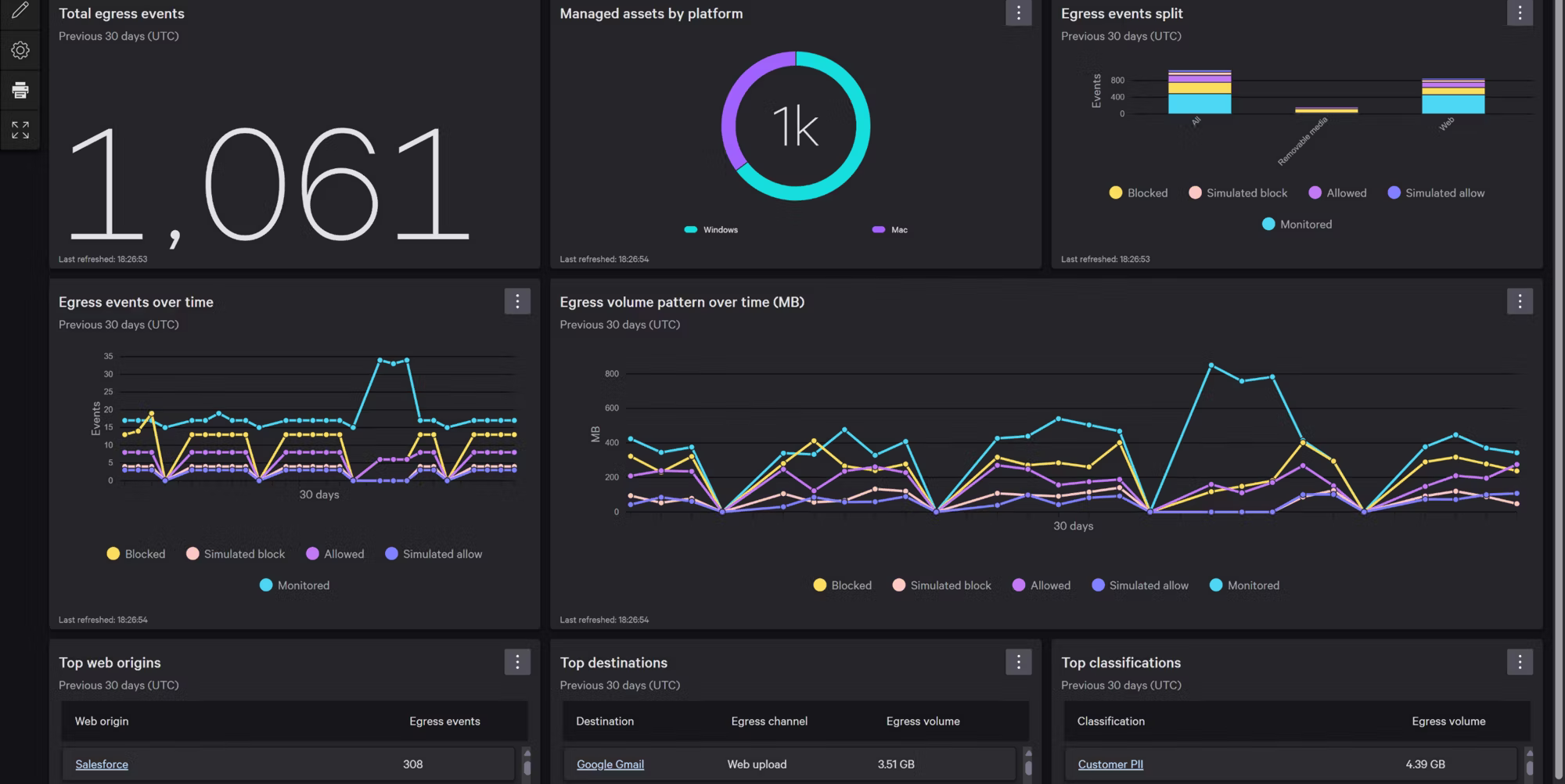
See all device activity
View comprehensive file metadata and activities across USB devices and SD cards, and Bluetooth and Thunderbolt devices on Mac to easily detect and investigate data loss and exfiltration. With detailed user and device information, ZIP archive introspection, and Microsoft sensitivity labels, you gain the visibility you need for a proactive defense.
Identify and safeguard source code
Detect source code movement with precision across all connected devices. Advanced machine learning watches over 40 source code languages, catching any sign of exfiltration through any supported connection type. Simple, effective, and relentless — your intellectual property is safeguarded against threats.
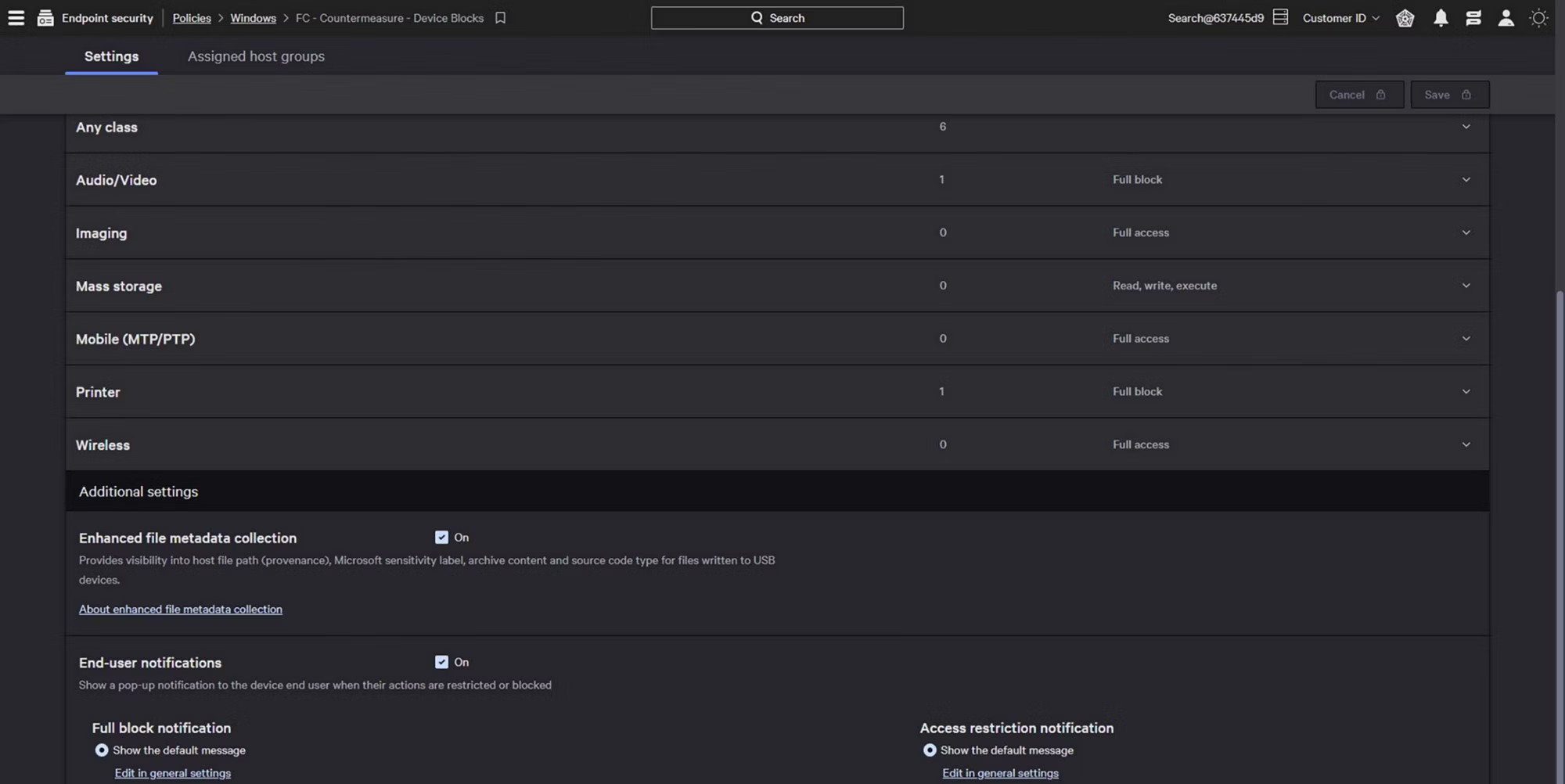
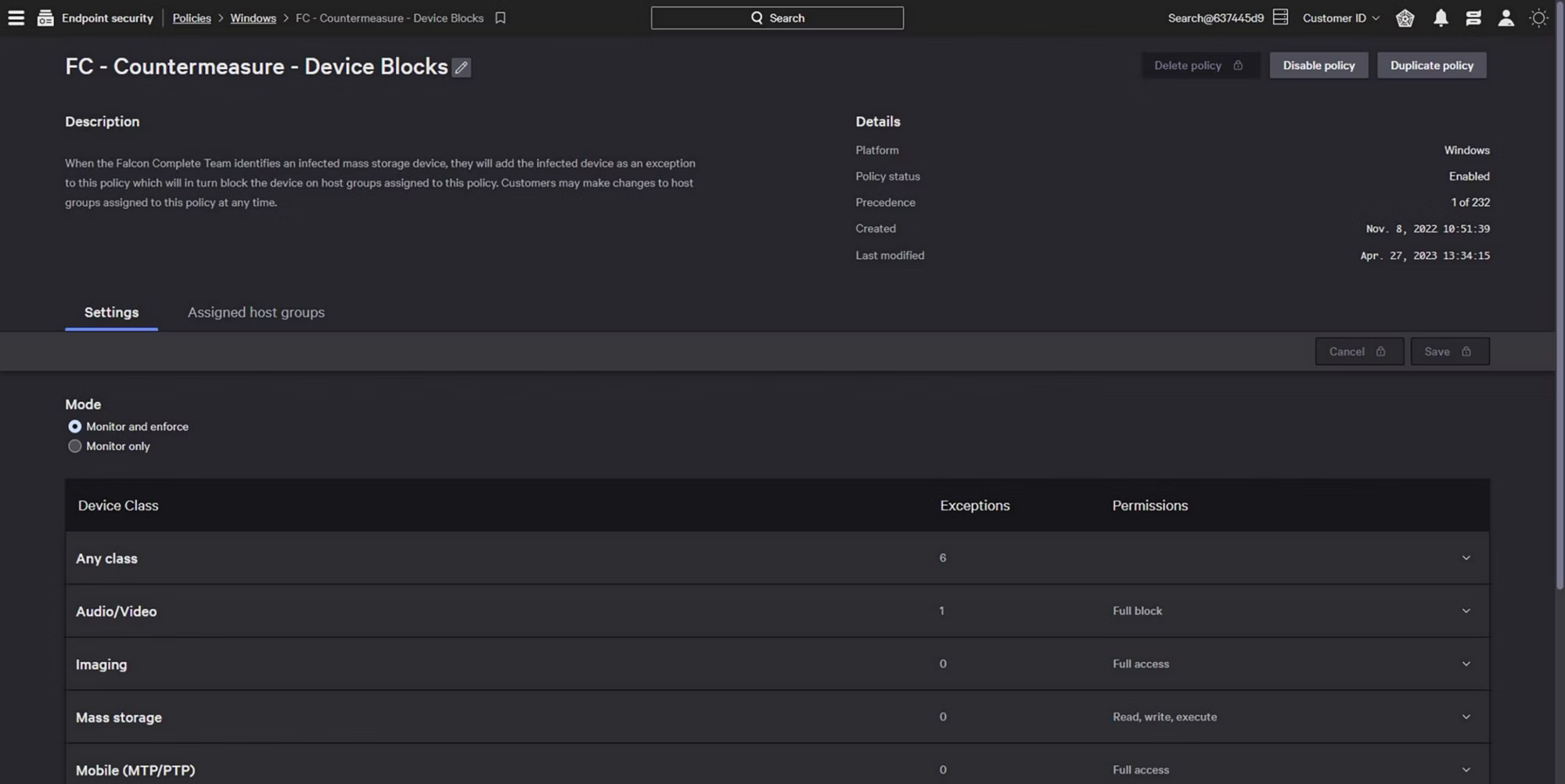
Precise and granular control
Implement granular access rights to ensure only approved external devices are used. Simple workflows accelerate policy creation and allow analysts to test policy impacts prior to enforcement, eliminating potential disruption across supported device types.
Cross-platform protection
Secure devices across both Windows and Mac environments with consistent policies and visibility. Control USB and SD card readers across all endpoints, plus Bluetooth and Thunderbolt connections on Mac systems. Maintain security standards across your entire organization with unified management, regardless of operating system.
THE BENEFITS
Mitigate malware risk
Gain the granular control needed to enable safe device use and prevent the spread of malware across all connection types, including USB, SD card, Bluetooth and Thunderbolt.
There's a lot more to [EPP] than just prevention, there's also reporting, threat hunting, and a lot of other things that go on top of that and those also need to be easy to use. So that's what pushed us towards CrowdStrike. The ease of deployment, the efficacy of the actual solution itself, it can do things at the speed you need them to be in today's world."
Kashif Parvaiz, CISO
Security gaps? We got you.
Sign up for our monthly email newsletter for expert insights on MDR, threat intel, and security ops—straight to your inbox.